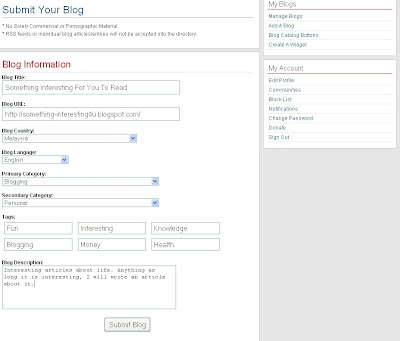
To Sign Up Paypal Account, Click Here.
Step by step video guide to sign up a paypal sandbox account.
Before you implement your online transactions using Paypal in live site, it is better for you to check the integrity of your coding in Paypal Sandbox.
You could make demo transactions in safe mode. Once you codes are free from errors, you could enable Paypal as one of the payment methods for your online store.
Paypal Sandbox is almost the same with live Paypal. It has all the features of Paypal.
You could create test buyer and seller accounts. You could create paypal buy now button, donate button and also integrate your e commerce shopping cart payment with paypal.
It is the best place for you to familiarize yourself with Paypal.
One the benefit of using Paypal is the ease of integration. You have Paypal Sandbox and lot of developers who are well verse in this field.
Plus, there are there a lot e commerce shopping carts that you could integrate with ease with Paypal.
List of popular ecommerce shopping carts that supports Paypal .
1. Oscommerce - one the most popular open source shopping cart.
2. Zen-Cart
3. Magento
4. CubeCart
For the complete list of shopping carts that support Paypal, click here.
All the integration you could test it in Paypal SandBox. Once ready and error free then only make it live.
Click here, to download Paypal SandBox User Guide (PDF)
To Sign Up Paypal SandBox account, click here.